I am integrating AD B2C as Identity provider for the FreshWorks by configuring SSO with OIDC in the Freshworks.
Configuration done in the Azure AD B2C:
-
Registered an application in the
AD B2C Tenanta. Get the redirect URL from Freshworks SSO with OIDC and added in the Redirect URI in the registered application
b. Id Tokens and Access Tokens check box is selected.
c. Enabled the public client.
d. Generate the client secret for the application
-
Added Microsoft as external IdP in the AD B2C tenant. Only one external IdP is enabled, local account is not enabled.
-
Created a SignupSign User flow
-
Tested the User flow, able to signup and sign-in using Microsoft Account (personal account). JWT token is generated with the claims sub, email, name.
Configuration done in the SSO with OIDC:
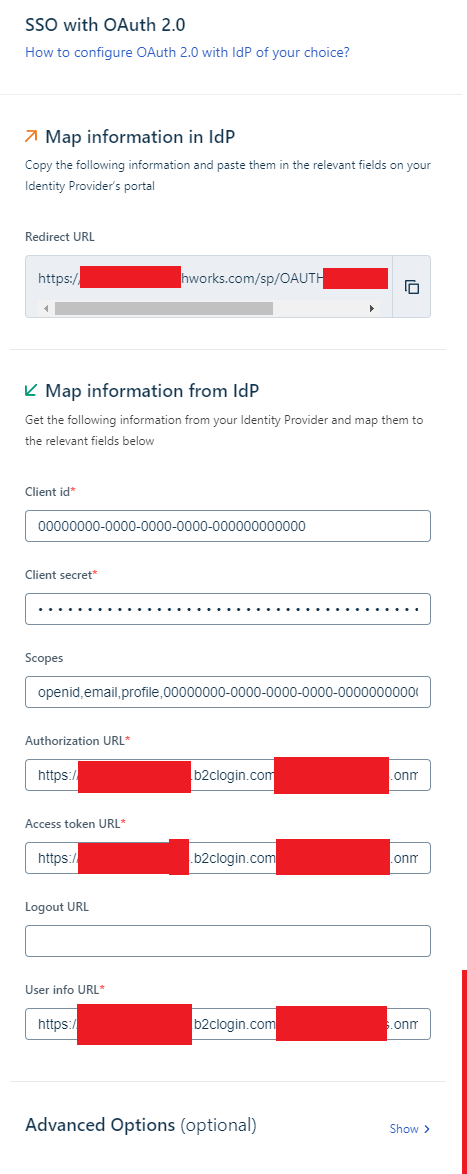
- Get the ClientId and Client Secret of the Application registered in the AD B2C tenant and added in the SSO with OIDC configuration dialog
- Navigate to AD B2C signup sign-in user flow OIDC configuration url and get the authorization_endpoint and token_endpoint, added those two in the SSO with OIDC configuration dialog
- set the scopes as openid,email,profile
After doing all the above configurations, a new button is added in the freshworks login page. I have clicked that button, it navigates to the microsoft login page, after providing credentials and accepted the consent, it shows a form with profile information. On clicking the continue button an account is created in the AD and redirected to the Freshwork page. It shows the below error in the freshworks login page.
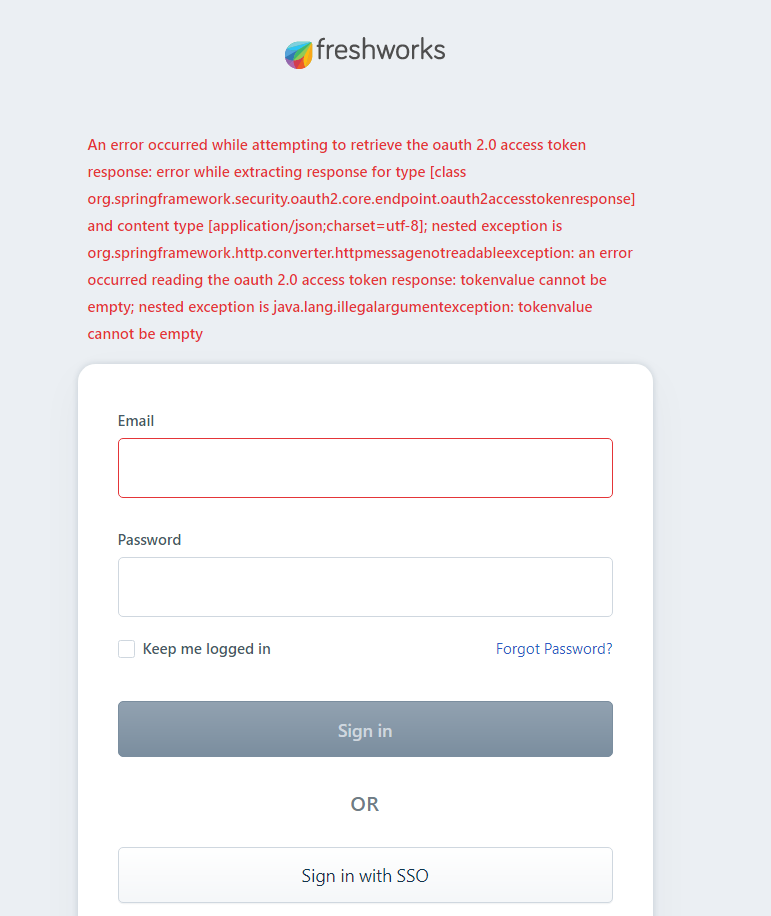
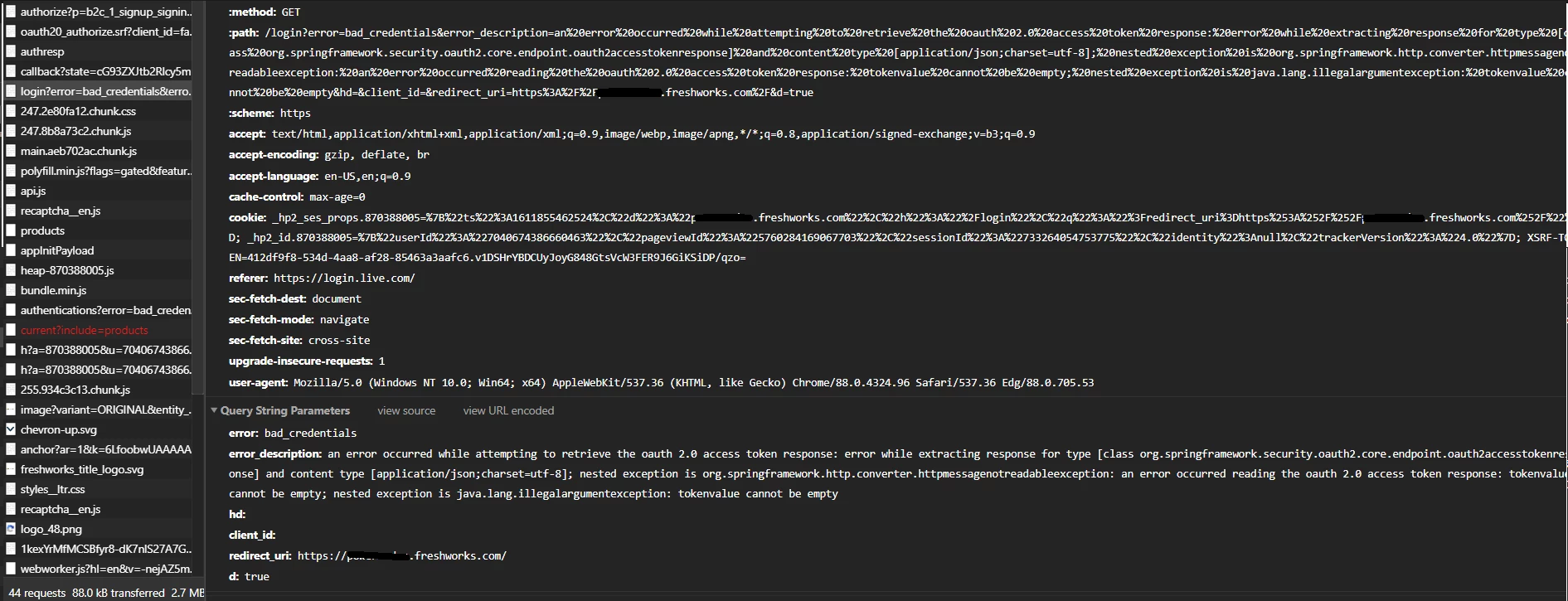
The authorization code request is working, AD B2C post the authorization code to the freshwork redirect url. I hope the issue is with the get access token endpoint URL. I have tried the Get access token endpoint from the postman using the authorization code received from the first request, it gives the access token.
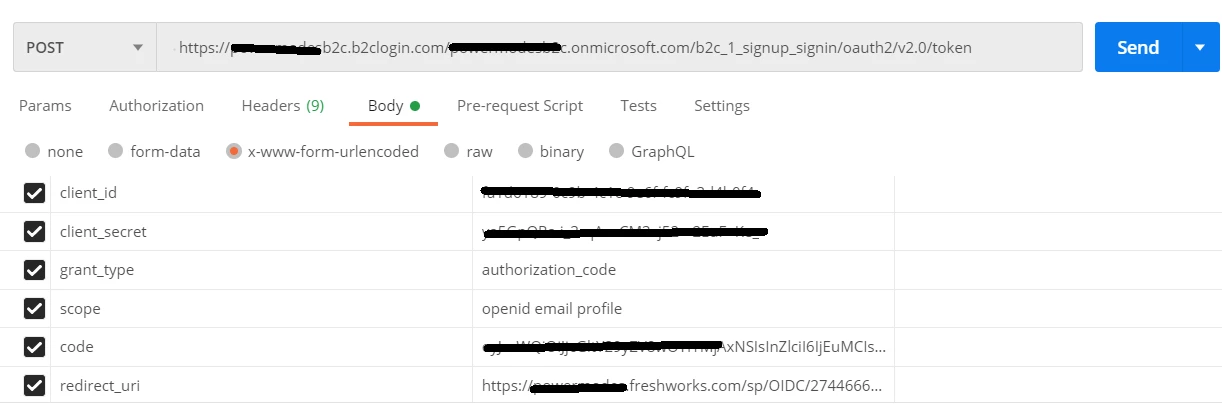
Please let me if there is any issue in the configuration. If you need additional details, please let me know. Help me to resolve this issue.
Best answer by hemanth.ramya
View original