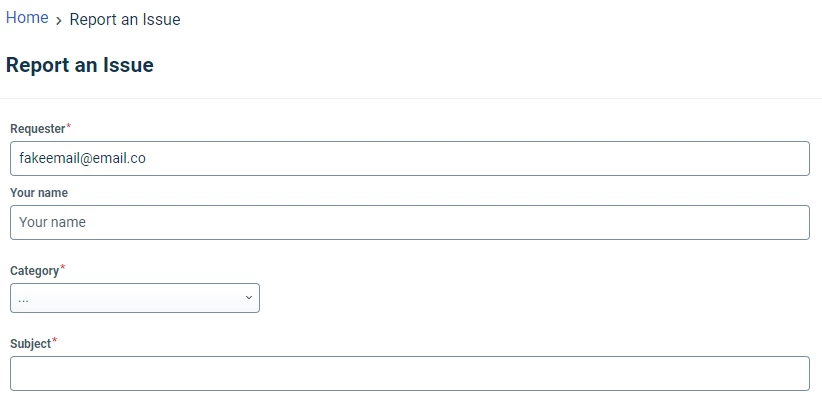
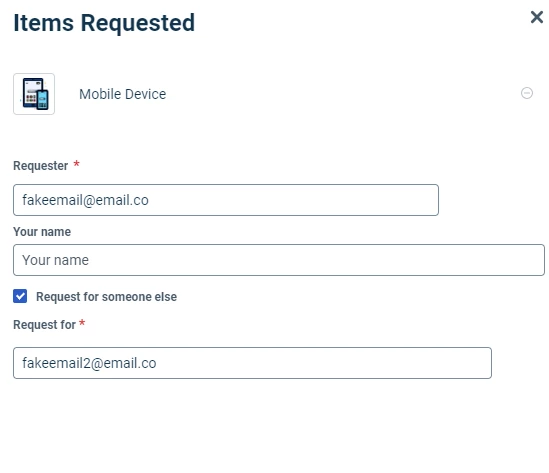
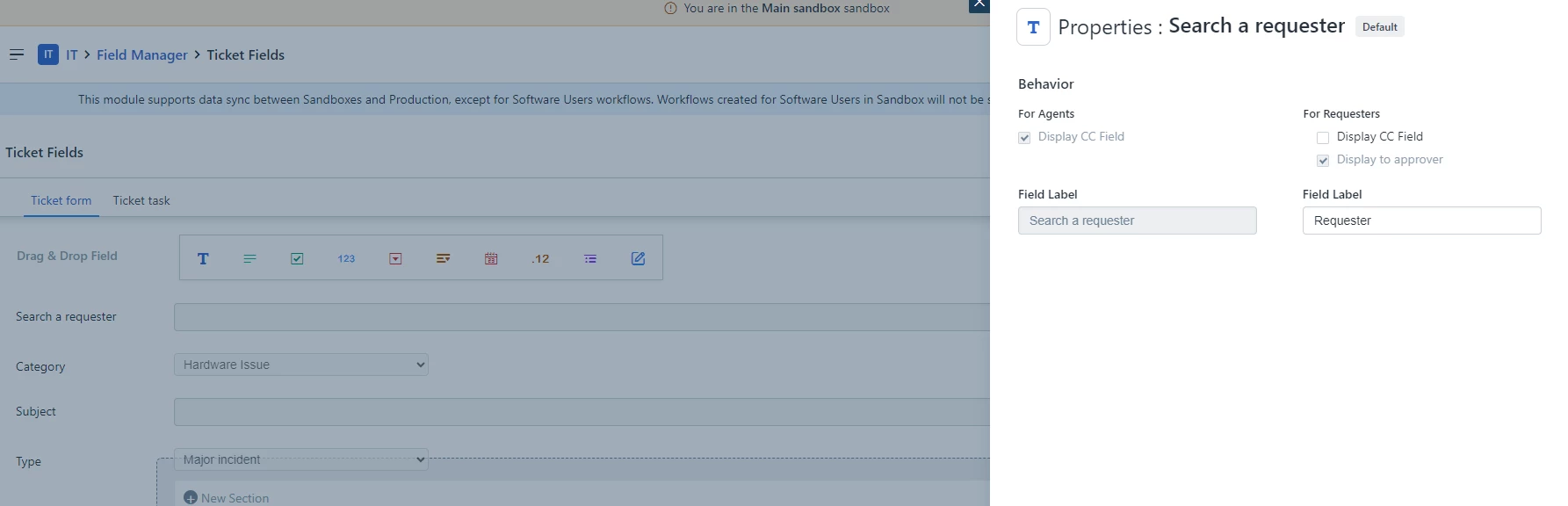
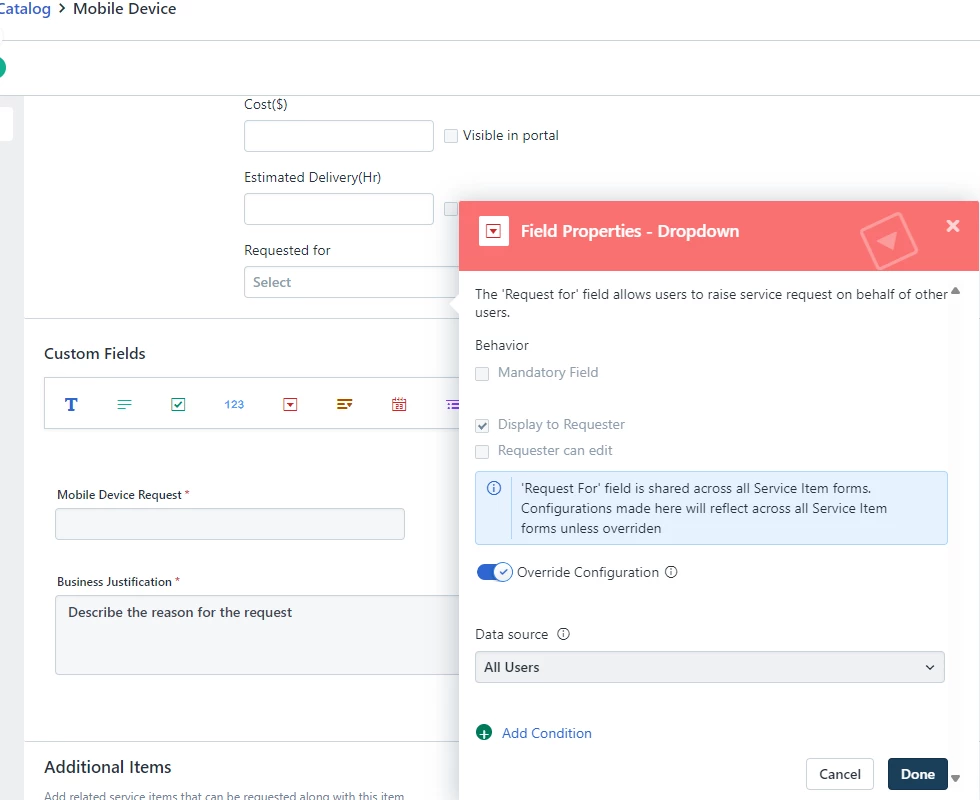
We have the need to restrict the Requester/Request For fields to only allow entries for existing users. Does this functionality currently exist in the system?
For further context, we have an import in place that pulls in all users that would need access to the system and/or have a ticket created for them. Since we already have the user list populated, we don’t want anyone submitting a ticket using an external email since it messes with our approval workflows.