Hi,
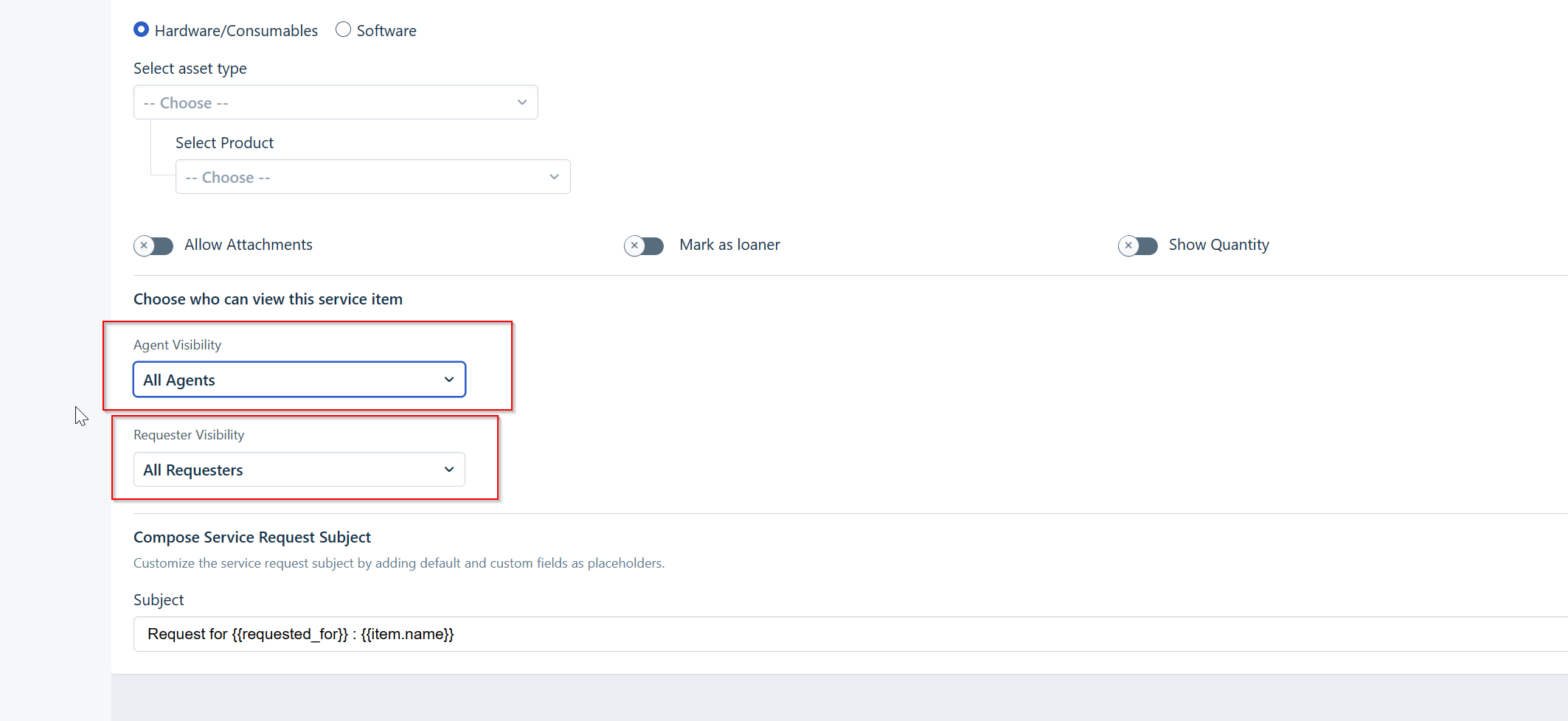
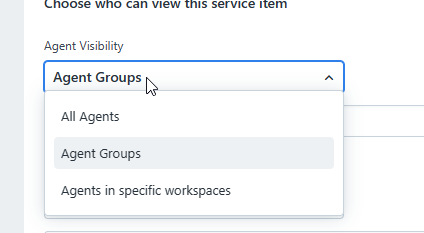
Is there a way that I can set “visibility” rules on Service Items that applies for all users, i.e. Requester + Agents?
I can’t find a way. If I for example would like to publish a service item for users in a specific location I would like that rule to apply all users but I do not understand how to achieve that.
We have quite many Agents spread across many departments and geographical locations and it will be difficult over time if we can not apply the same rules for them as they as employees in many situations are Requesters.